No matter what you do for a living, you deal with all kinds of risks daily — whether it’s operational hiccups, financial uncertainty, or potential reputation hits.
But it’s the unexpected curveballs you don’t see coming, like a sudden cybersecurity breach or equipment failure, that really shake things up.
Trust me; I’ve been there.
That’s where a risk assessment comes in.
With it, I can spot, analyze, and prioritize risks before they turn into full-blown problems. I can get ahead of the game, so that when the unexpected strikes, I already have a plan in place to keep things under control.
In this guide, I’ll share tips for running a risk assessment in five easy steps. I’ll also feature a customizable template to help you sharpen your decision-making.
Table of Contents
What is a risk assessment?
A risk assessment is a step-by-step process used to identify, evaluate, and prioritize potential risks to a business’s operations, safety, or reputation.
It helps businesses understand the threats they face and determine how best to manage or reduce those risks.
The risk assessment process involves identifying hazards, assessing how likely they are to occur, and evaluating their potential impact.
With this information, businesses can allocate resources effectively and take proactive measures to avoid disruptions or accidents.
Purpose and Benefits of Risk Assessments
At its core, a risk assessment is all about identifying potential hazards and understanding the risks they pose to people — whether they’re employees, contractors, or even the public.
By doing a deep dive into these risks, I can take action to either get rid of them or minimize them, creating a much safer environment. And sure, there’s the legal side — many industries require it — but beyond that, it’s about proactively looking out for the health and safety of everyone involved.
It‘s important to note how crucial risk assessments are for staying compliant with regulations. Many industries require businesses to conduct and update these assessments regularly to meet health and safety standards.
But compliance is only one side of the coin. Risk assessments also show the company genuinely cares about its employees’ well-being.
Benefits of Risk Assessments
Think of a risk assessment template as your business’s trusty blueprint for spotting trouble before it strikes. Here’s how it helps.
Awareness
Risk assessments shine a light on the risks lurking in your organization, turning risk awareness into second nature for everyone. It’s like flipping a switch — suddenly, safety is a shared responsibility.
I’ve seen firsthand how, when people feel confident enough to call out risks, safety compliance just clicks into place. That’s when you know the whole team is looking out for each other.
Measurement
With a risk assessment, I can weigh the likelihood and impact of each hazard, so I’m not shooting in the dark. For instance, if I find that one task is particularly risky, I can change up procedures or workflows to bring that risk down.
Results
The real magic happens when you act on your findings. By catching risks early, I can prevent different types of crises like machine breakdowns or workplace accidents — things that can quickly spiral out of control.
Not only does this safeguard employees and minimize the fallout from those risks, but it also spares your organization from costly legal troubles or compensation claims.
When should you conduct a risk assessment?
Here are the most relevant scenarios for conducting a risk assessment.
Before Introducing New Processes or Products
If I’m launching a new product or service, I’d want to assess all the potential risks involved. This could include safety risks for employees, financial risks if the product doesn’t perform as expected, or even supply chain risks.
For example, as a manufacturer, you might evaluate the risks of new machinery affecting production lines.
After Major Incidents
If something goes wrong, like a data breach or an equipment failure, a risk assessment again comes in handy. I can better understand what went wrong and how to prevent it from happening again.
For example, after a data breach, an IT risk assessment could reveal vulnerabilities and help bolster defenses.
To Meet Regulatory Requirements
Staying compliant with industry regulations is another big motivator. In industries like healthcare or finance, this could mean avoiding hefty penalties or fines.
Compliance frameworks like HIPAA risk assessment in healthcare or OSHA for workplace safety make regular risk assessments a must.
When Adopting New Technologies
Integrating new technologies, such as IT systems or machinery, can introduce new risks. I recommend conducting a risk assessment to identify any potential cybersecurity or operational risks.
Without this, your business could be exposed to new vulnerabilities.
When Expanding Operations
Whenever expanding into new markets, it’s essential to assess potential risks, especially when dealing with different local regulations or supply chains.
Financial institutions, for example, assess credit and market risks when they expand internationally.
Pro tip: Don’t wait for problems to arise — schedule regular risk assessments, either annually or bi-annually. This keeps you ahead of potential hazards and ensures you’re constantly improving safety measures.
Types of Risk Assessments

When conducting a risk assessment, the method you choose depends on the task, environment, and the data you have on hand. Different situations call for different approaches.
Here are the top ones.
1. Qualitative Risk Assessment
This assessment is suitable when you need a quick judgment based on your observations.
No hard numbers here — just categorizing risks as “low,” “medium,” or “high.” It’s perfect for when you don’t have detailed data and need to make a call based on experience.
For example, when assessing an office environment, like noticing employees struggling with poor chair ergonomics, I should label that a “medium” risk. Sure, it impacts productivity, but it’s not life-threatening.
It’s a simple approach that works well for everyday scenarios.
2. Quantitative Risk Assessment
When you have access to solid data, like historical incident reports or failure rates, go for a quantitative risk assessment.
Here, you’ll assign numbers to both the likelihood of a risk and the potential damage it could cause. This makes the assessment a more precise way of evaluating risk, especially for industries like finance or large-scale projects.
Take, for instance, a machine that breaks down every 1,000 hours, costing $10,000 each time. With this assessment, I can calculate expected annual costs and decide if it’s smarter to invest in better maintenance or just get a new machine.
3. Semi-Quantitative Risk Assessment
This is a blend of the first two.
In this risk assessment method, you assign numerical values to risks but still categorize the outcome as “high” or “low.” It gives you a bit more accuracy without diving into full-blown data analysis.
At HubSpot, leadership used this when relocating an office. The team couldn’t exactly quantify the stress employees would feel.
By assigning scores (like 3/5 for impact and 2/5 for likelihood), leaders got a clearer picture of what to tackle first — like improving communication to ease the transition.
4. Generic Risk Assessment
A generic risk assessment addresses common hazards that apply across multiple environments.
It’s best for routine or low-risk tasks, such as manual handling or standard office work. As the risks are well-known and unlikely to change, you don’t have to start from scratch every time.
When dealing with manual handling tasks in an office, for example, the risks are pretty standard. But you must always stay flexible, ready to tweak your approach if something unexpected comes up.
5. Site-Specific Risk Assessment
A site-specific risk assessment focuses on hazards unique to a particular location or project.
For example, if you‘re evaluating a chemical plant, for instance, don’t just rely on generic templates. Instead, consider the specifics: the chemicals used, the ventilation, the layout — everything unique to that site.
By doing this, you can address unique hazards and often high-risk environments, like suggesting better spill containment measures or retraining employees on safety procedures.
6. Task-Based Risk Assessment
In a task-based risk assessment, focus on specific jobs and the risks that come with them. This is ideal for industries like construction or manufacturing, where different tasks (e.g., operating a crane vs. welding) come with varying risks.
As each task gets its own tailored assessment, don’t miss the unique dangers each one brings.
How to Conduct a Risk Assessment for Your Business

When I need to run a risk assessment, I like to rely on a handy guide. Here’s a more comprehensive look at each step of the process.
1. Identify the hazards.
When identifying hazards, I try to get multiple perspectives so that I don’t miss any hidden risks.
Here’s how I go about it:
- Talking to my team. Since my team is the one dealing with hazards daily, their insights are invaluable, especially for identifying risks that aren’t immediately obvious.
- Checking past incidents. I review old accident logs or near-misses. Often, patterns emerge that highlight risks I may not have considered before.
- Following industry standards. If you work in certain industries, OSHA guidelines or other relevant regulations provide a solid framework to help spot hazards you might otherwise overlook.
- Considering remote and non-routine activities. I make sure to assess risks for remote workers or non-regular activities, like maintenance or repairs, which can introduce new hazards.
For example, during a system audit, I might identify obvious risks like unsecured servers or outdated software.
However, I must also consider hidden risks, such as unsecured Wi-Fi networks that remote employees might use, potentially exposing sensitive data.
Reviewing past incident reports, like past phishing attempts or data breaches, may reveal both technical and human-related vulnerabilities.
By taking all these factors into account, you can better protect your data and keep operations running smoothly.
2. Determine who might be harmed and how.
In this step, I widen my focus beyond just employees to include anyone who might interact with my daily operations. This includes:
- Visitors, contractors, and the public. That includes anyone who interacts with operations, even indirectly, is considered. For instance, construction dust on-site could harm passersby or visitors.
- Vulnerable groups. Certain people — like pregnant workers or those with medical conditions — might have heightened sensitivities to specific hazards.
Take the unsecured server example mentioned earlier. IT staff might be aware of the risks, but I also need to consider non-technical employees who might not recognize phishing emails.
3. Evaluate the risks and decide on precautions.
As I evaluate risks, I focus on two main factors: how likely something is to happen and how severe the impact could be.
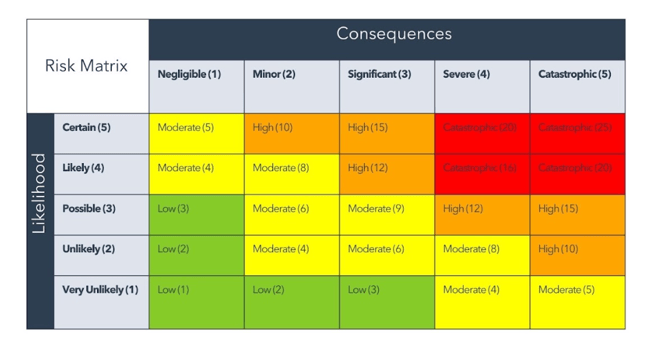
- Use a risk matrix. The risk matrix isn’t just a tool to categorize risks but a strategic guide to help me decide which business risks need action now and which can wait. I focus first on high-probability, high-impact risks that need immediate action, and then work my way down to those that can wait.
- Determine the root causes. Next, I want to understand why a risk exists — whether it’s outdated software, lack of cybersecurity training, or weak password policies. This will help me address the issue at its core and create better solutions. Consider using a root cause analysis template to help you systematically capture details, prioritize issues, and develop targeted solutions.
- Follow the control hierarchy. The hierarchy of controls provides a structured approach to managing hazards. My first priority is always to eliminate the risk, like disabling unused access points. If that’s not possible, I implement network segmentation, multi-factor authentication, or encryption before relying on user training as a last line of defense.
For example, when dealing with phishing risks, frequent incidents and inconsistent training were the main concerns. To mitigate them, I could start by providing more robust training and enforcing multi-factor authentication. I could implement email filtering tools to reduce phishing emails.
If that’s not an option, I can improve response protocols. Incident response plans would provide additional protection.
4. Record key findings.
At this stage, it’s time to document everything: the risks identified, who’s at risk, and the measures put in place to control them. This is especially crucial if you’re operating in a regulated industry where audits are a possibility.
Here’s how to lay out the documentation based on our earlier example.
- Hazards identified: Phishing attempts, unsecured servers, data breach risks.
- Who is at risk: Employees, customers, third-party vendors.
- Precautions: Multi-factor authentication, email filters, encryption, regular cybersecurity training.
Pro tip: Digitize these records and include photos of the relevant areas and equipment. This will keep you compliant with regulations while also doubling as an excellent risk assessment training resource for new employees. Plus, it ensures everyone can access the information when needed.
5. Review and update the assessment.
Risk assessments aren’t a “set it and forget it” thing. That‘s why I recommend reviewing your assessment plan every six months — or whenever there’s a significant change.
Here’s how to approach it:
- Trigger a review with changes. Whether it’s new equipment, new hires, or regulatory updates, any major shift calls for a reassessment. For example, after upgrading a cutting machine, I can immediately revisit the risks to address updated training needs and potential software issues.
- Incorporate ongoing feedback. Employee input and regular audits play a huge role in keeping assessments up to date. By maintaining open communication, you can spot new risks early and ensure existing safety measures remain effective.
Free Risk Assessment Template
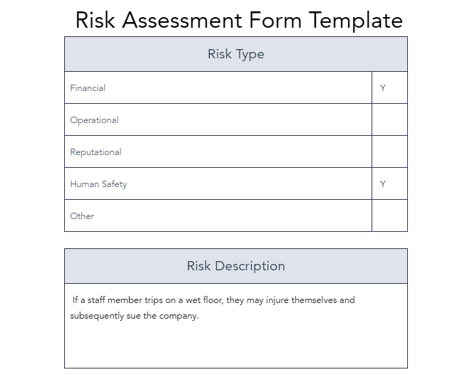
Need a quick, easy way to evaluate different risks — like financial or safety risk? HubSpot’s got you covered with a free risk assessment template that helps you outline steps to reduce or eliminate those risks.
Here’s what our template offers:
- Company name, person responsible, and assessment date.
- Risk type (financial, operational, reputational, human safety, etc.).
- Risk description and source.
- Risk matrix with severity levels.
- Actions to reduce risks.
- Approving official.
- Comments.
Grab this customizable template to assess potential risks, gauge their impact, and take proactive steps to minimize damage before it happens. Simple, effective, and to the point!
Take Control of Your Workplace
Effective risk assessment isn’t just about ticking a compliance box—it’s a proactive way to keep your business and employees safe from avoidable hazards.
Always start by identifying specific risks, whether they‘re tied to a particular site or task. Once you’ve got those, prioritize them using tools like a risk assessment matrix or a semi-quantitative assessment to make sure you’re tackling the most pressing issues first. And remember, it’s not a one-and-done thing—regular reviews and updates are crucial as your business evolves.
Plus, with HubSpot’s free risk assessment template on hand, you’ll always have a strong foundation to stay one step ahead of any potential risks.
![]()